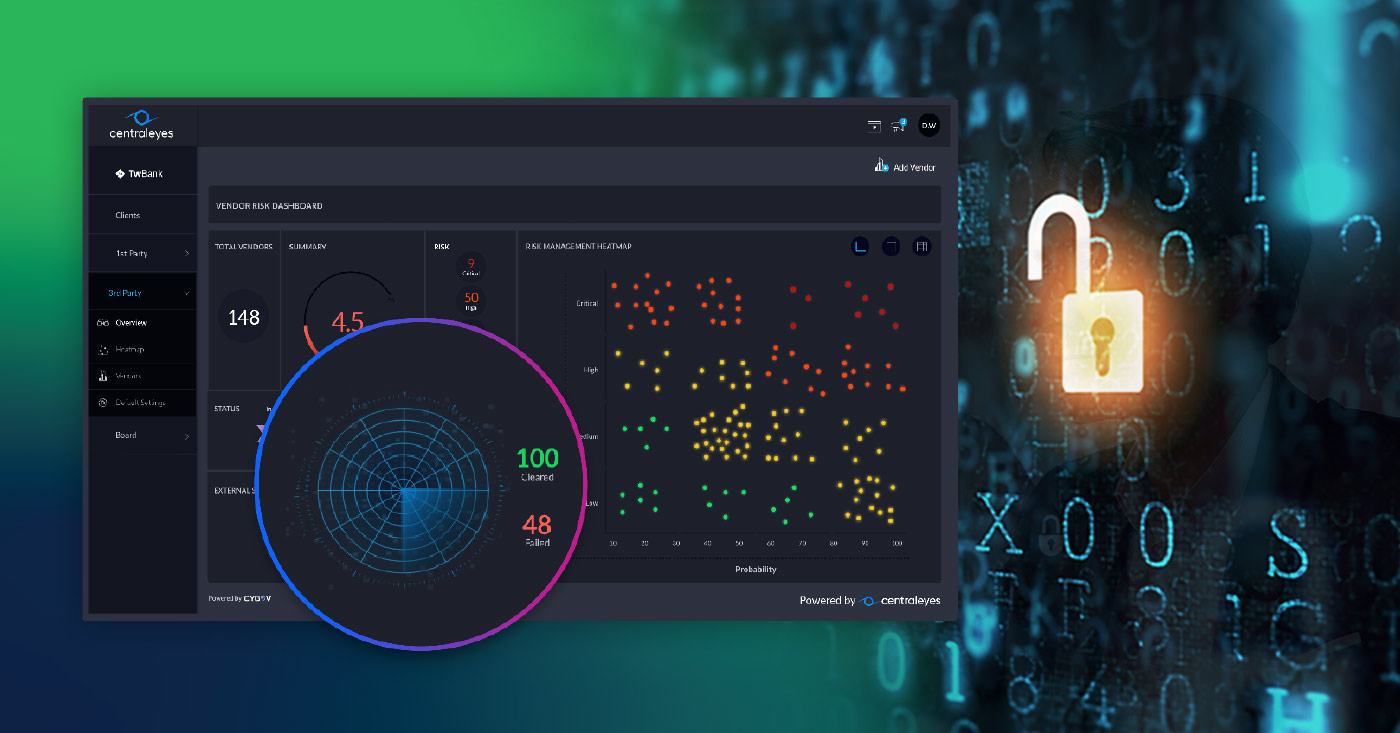
Third-party vendors have always been a key part of success, and with the rise in service providers and ‘anything as a service’, this is more true today than ever before.
But vendors can also create unexpected challenges for your business, not the least of which are cybersecurity risks.
This post will cover the unique risks that vendors can pose to your business and how you can guard your business against these risks.
The risks vendors pose to cybersecurity
Cybersecurity risk

As mentioned, one of the core risks that a third-party vendor creates for your business is cybersecurity risk. There are two primary ways that a vendor can create cybersecurity risk for your business.
First, sharing sensitive information with a vendor can prove risky. This creates an additional copy of data, doubling its vulnerabilities. If the vendor in question has poor cybersecurity policies, your risk only increases.
The second risk is networking. If a vendor has access to your network to provide you services, that connection can be exploited by a bad actor. In other words, a network breach for your vendor could lead to a network breach for you.
Compliance risk

These days, companies are concerned with keeping their cybersecurity policies strong against attacks and compliant with current regulations. The challenge with vendors is that you can have limited insight into their regulatory compliance.
If you’re working with a vendor that isn’t compliant, it can affect your compliance as well. If they’re not securing data as they should, networking properly, or authenticating users with approved protocols, then by extension, neither are you.
Reputation risk

In some ways, any kind of security risk that a vendor presents doubles as reputation risk. Companies affected by cybersecurity breaches are deemed non-compliant by regulators or that face other types of threats are also likely to suffer blows to their public reputation.
Working with a vendor that already has a bad reputation (or could potentially develop one) can result in that image rubbing off onto your business. It’s vital to vet a vendor’s reputation before doing business with them.
Financial risk

Financial risk occurs when a vendor directly influences a portion of your finances or is collecting, monitoring or reporting your financial data. These services can be as helpful as they are harmful.
For instance, a vendor billing your business and promising to provide a certain ROI percentage could be failing to do so without you knowing it. This could lead to a decrease in your overall revenue, and it would be difficult to pin down why from your side of things.
Another possibility is that a vendor who monitors and reports your finances could be reporting false numbers. This could be due to a mistake, a bad actor, or potentially even fraud.
Operational risk

While some of the risks mentioned in this post might be exclusive to one vendor or another, operational risks can come from any vendor you depend on because your operations are linked with theirs.
If the vendor you’re working with has to shut down, pause, or restructure their operations for any reason, this could hamper your ability to provide a critical service or product.
Strategic risk

Strategic risks occur whenever a vendor can make strategic decisions on your business’s behalf. For instance, a vendor might make a decision that affects your reputation or impedes your goals.
Understanding how much control each of your vendors has is key. Otherwise, a vendor could make a significant decision without your input or control.
Why it’s important to manage your vendor security, and how JT can help
JT offers various risk protection services, including vendor assessments for determining and counteracting the risks posed by your vendors. Below are two key ways we can help.
Use JT’s risk assessment framework
JT offers a risk assessment framework that uses industry standards like ISO27001 and NIST SP800-53. This service gives you an accurate and holistic view of how each of your vendors impacts your risk potential.
This risk assessment framework analyses financial, operational, strategic, and compliance risk factors. You can use it to predict and reduce the potential harm a vendor can do to your business, intentionally or otherwise.
Take advantage of the modules in the JT Centraleyes Compliance Platform
We also offer a JT Centraleyes Compliance Platform. This platform offers a variety of compliance and cybersecurity features, and works together with our risk assessment framework. That means customers can access all modules in both systems, providing maximum support.
Reach out to JT today and see how the JT Centraleyes Compliance Platform can reduce your vendor risks.