|
Author: Nelson Ody Security Product Manager |
Cyber threats are an ever-evolving danger to our businesses and personal lives and as more services move online, the threat to both our personal and business data has never been higher. Everything from your computer to your toaster is now connected to the internet, meaning over the past few years, the possible avenues for exploitation by malicious individuals have multiplied dramatically.
Keeping on top of digital hygiene is our best chance at keeping threats at bay, but what does good digital hygiene look like? Read on to learn exactly what digital hygiene is, it’s benefits and some best practices for implementing it into your security environment.
Jump to a section:
What is digital hygiene?
Digital hygiene is a series of steps users of digital devices can take to improve their online security and maintain system health. The key to implementing a strong level of cybersecurity hygiene is to adopt a security-centric mindset. In other words — “what can I do to ensure my system is secure?”.
Developing good habits can help your system just as much as the software you use to combat threats. The more you think about how your actions affect cybersecurity, the better prepared you can be. Common sense measures such as avoiding suspicious links, protecting your personal information, and avoiding downloading files from untrusted sources are key parts of digital hygiene.t
The emphasis on digital hygiene has increased with a greater attention on general hygiene post-pandemic. It’s been well documented that the increase in remote work has opened the door for cybercriminals and highlighted how important it is for every individual who interacts with a network or system — be that at home or at work — to understand their role in maintaining cybersecurity.
The benefits of Digital Hygiene
Let’s look at some of the steps you can take and their benefits.
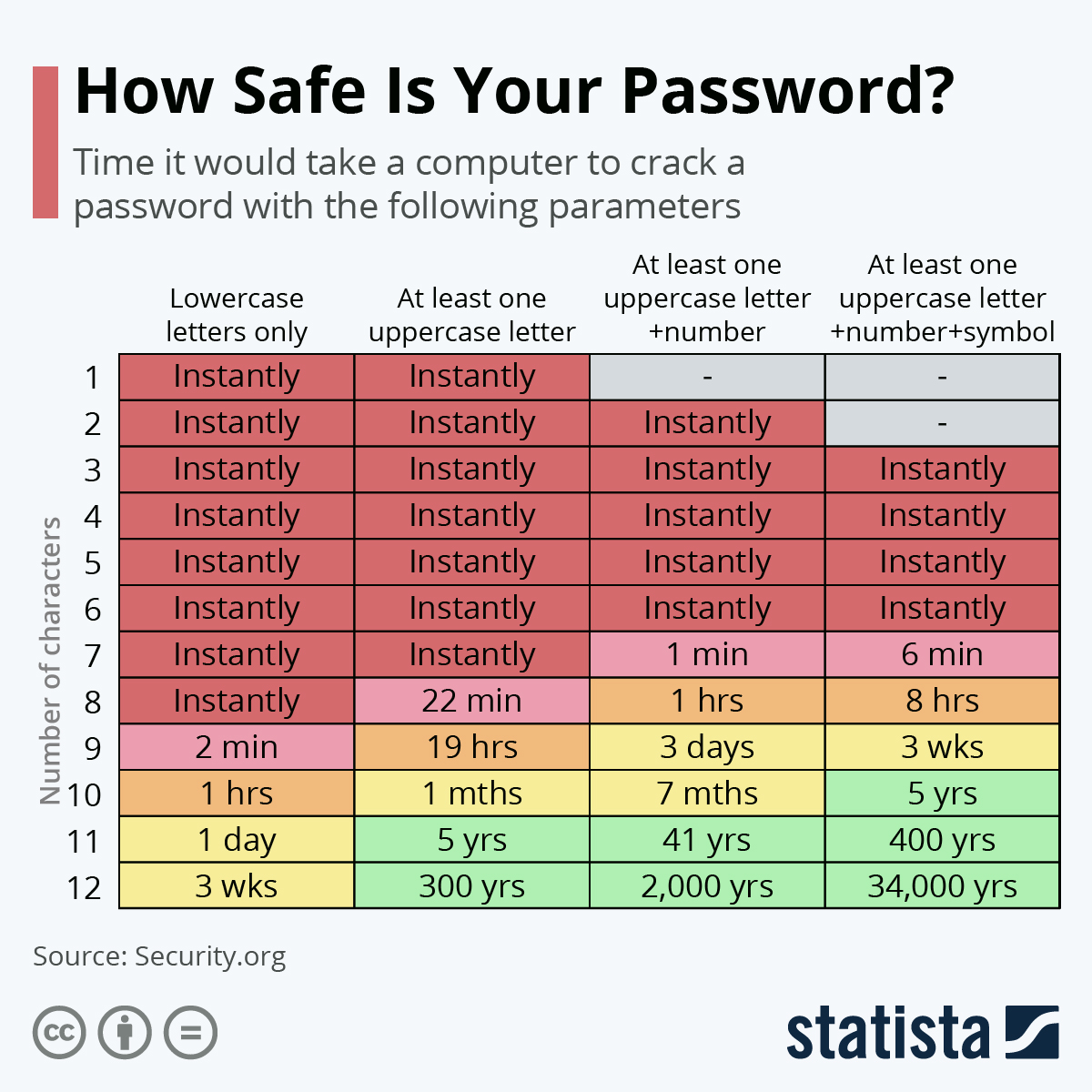
Password policies
The very concept of passwords is on its way out according to 79% of respondents questioned at the 2023 BlackHat USA Conference in Las Vegas. But until viable solutions become mainstream, passwords are still a core part of almost every app, software program, and website.
Passwords contribute a sizable risk to businesses and personal accounts as weak ones are responsible for 35% of data breaches. That’s over a third of all breaches caused by an easily remedied issue. Despite the risk involved, many still fail to take the need for strong passwords seriously.
It’s not a lack of awareness that is contributing to this problem. 92% of people are aware that using the same password or a variation of it presents a risk, yet 65% continue to do just that. Password managers have helped with this, offering unique, secure passwords upon signup and saving them, but 51% are still relying on memory alone to keep track of passwords.
Patching regime
This is another area where awareness is high, but action is low. Roughly 75% of organisations are aware of the risk involved with unpatched software, yet just 50% have a documented process for patch management.
A study by Microsoft discovered that timely patching could prevent over 80% of successful cyberattacks, reducing overall downtime while also avoiding reputational damage, lost business, and regulatory fees.
Online discretion
Social media has become an incredibly large part of our daily lives. While mostly harmless, it has led to a culture of oversharing which can have damaging effects when it comes to personal and organisational security.
Oversharing on social media has unfortunately led to an increase in social engineering attacks, which account for 98% of all cyberattacks. Yet it’s not a trend that is going away any time soon. A report from Tessian found that 84% of people post personal information to their social media accounts every week, with two-fifths (42%) posting every day. It's such a significant part of modern culture that we need to look at mitigating the threat as we cannot eliminate it entirely.
This level of oversharing has also led to a rise in identity theft cases over the past few years. The huge amount of information available to bad actors simply from scrolling through social media profiles makes this kind of threat relatively easy to pull off. Sharing even innocuous-seeming information, such as a picture of a passed driving certificate, can allow bad actors to gain access to accounts and lead to identity theft.
For organisations, social media policies are crucial. Implement rules surrounding posting company information to social media to avoid it falling into the wrong hands.
Rebooting schedule
Most people know that regularly rebooting and shutting down your PC can reduce energy consumption, free up memory, and improve RAM performance, but few realise the security benefits it can bring.
Regular reboots give your operating systems a chance to install crucial software updates, many of which require restarting the system to take effect. Implementing a schedule for your restarts will ensure the system can deploy security patches on a regular basis and improve performance without disrupting your work.
Smishing
Smishing is another type of cyber attack that is on the rise globally. A portmanteau of the words “SMS” and “phishing”, smishing involves bad actors gaining access to personal data through the use of SMS.
Since most smartphones are able to receive messages from any number in the world, the number of targets is astronomical. Much like in traditional phishing attacks, bad actors will send links to follow or advise actions to be taken by the receiver of an SMS. Depending on the exact type of attack, this will then allow them access to the receiver’s personal data resulting in a breach.
Insider threats
An often overlooked part of digital hygiene is ensuring everyone in the organisation is aware of the threats they face. Education is crucial to get everyone on the same page and eliminate easily avoided threats from affecting the organisation.
While many may feel they’re aware of the risks such as the ones we’ve already discussed, around 31% of all data breaches were caused by insider threats, with the average cost of an insider threat being roughly $8.76 million globally. So while it may seem like a waste of time, it doesn’t hurt to reinforce the message that personal actions make a huge difference to cybersecurity.
Threats your IT team might not know about
Cybersecurity education and awareness aren’t just for employees outside of the IT department. There may be cyber threats that even the IT department isn’t aware of, such as technical vulnerabilities inherent in the systems that are used by the organisation. It is important that IT specialists also educate themselves on the more complex and technical aspects of digital hygiene to ensure they can combat more advanced threats.
This is particularly important when it comes to cyber threats originating from the dark web. The dark web is an obscured portion of the internet made up of sites that cannot be accessed from normal web browsers. This makes combating threats that come from the dark web exceptionally difficult, even for trained IT specialists.
When optimising an organisation’s digital hygiene, it is key to not only focus on easy-to-address threats but also to take steps to ensure that systems are protected from sophisticated, well-coordinated attacks from bad actors often operating from the shadows of the dark web.
Best practices for businesses of all sizes
Let’s run through some essential best practices for businesses to improve their digital hygiene.
Use Strong, Unique Passwords
Until we see widespread use of passwordless technology, organisations must continue to emphasise the importance of password strength. Unique passwords with a mix of lowercase letters, uppercase letters, numbers, and special characters are required to avoid easy guesses.
Avoid repeating passwords across programs and accounts and avoid using guessable passwords that use birthdays or common words. Simply adding a 1 at the end of your password is not enough to deter cybercriminals. In fact, the UK National Cyber Security Centre (NCSC) recommends using three random words to create strong passwords that are more difficult to crack.
Enable Multi-Factor Authentication (MFA)
MFA offers an extra level of protection, so if someone does obtain your password, they’re still unable to access your account. The process usually involves the user entering a password followed by obtaining a code from something else such as SMS, hardware token, or an app such as Google Authenticator or the Microsoft 365 mobile app.
This should be deployed as standard throughout any organisation to ensure data is protected and bad actors are shut out. Where possible, it is ideal to implement biometric authentication as this is essentially impossible for bad actors to breach. This may not be possible on company-wide equipment but if employees have personal devices, biometrics should be employed if available.
MFA can also be used to protect personal data outside of work. It is worth considering setting up MFA on common apps that are used in the home, such as the Google Play store and Amazon. These apps have access to scores of personal information and may also be linked to business accounts, meaning a breach at home may lead to not only the loss of personal data but also organisational data.
Keep Software Up to Date
While regular updates may be slightly annoying, they are vital to ensuring your system is fully capable of withstanding threats. New cybersecurity attacks are created on a daily basis, meaning system managers should be vigilant and avoid falling behind on updates.
Implementing a reboot schedule and enabling automatic updates where possible will ensure your system remains up to date with security patches and avoid downtime.
Install and Update Antivirus Software
It should go without saying that organisations should have robust, reputable antivirus or anti-malware software in place. While the default OS-level software may be enough for personal devices, organisations need an extra level of protection. It’s crucial that antivirus software is updated regularly so it can monitor the latest threats in a fast-moving landscape.
Be Cautious with Email
Email clients have become far better at flagging potentially dangerous messages, but organisations should still be cautious. Social engineering attacks — when bad actors exploit human error to gain access to information or systems — are of particular concern due to the human aspect of this kind of threat.
Business email compromise is expected to rise over the coming years as social engineering attacks become increasingly sophisticated and prevalent. Education is crucial to help mitigate these attacks, as all employees need to be aware of the risk and potential red flags in any emails they might receive.
Avoid downloading attachments or clicking links from unknown senders, especially if they are unsolicited messages. When in doubt, make sure to verify the legitimacy of emails, especially those requesting sensitive information or money.
Educate yourself and others
As mentioned earlier, education is one of the best tools we have when it comes to improving digital hygiene. It shouldn’t be left to the IT team to keep track of cybersecurity developments as every individual on a network presents a risk.
Where possible, educate your family, friends, and colleagues about cybersecurity best practices to help protect them and create a safer online environment.
Secure your WI-FI network
A poorly secured WI-FI network provides a huge gateway to bad actors looking to steal data. Make sure your network has a strong, unique password and avoid using easily guessable phrases such as anything relating to the company. You should enable WPA3 encryption, hide your network's SSID, and regularly update your router’s firmware to ensure complete protection.
Backup your data
Regular backups of your data will ensure you don’t lose anything important if the worst does happen. You can use external devices or cloud-based services for this but be sure that your backups are encrypted and only accessible to authorised users.
Secure mobile devices
The prevalence of remote work has meant a wider number of mobile devices will be accessing your network. This makes it extremely difficult for security teams who now have to deal with a wide range of devices with varying levels of protection. Ensure mobile devices have strong PIN or biometric authentication, only download verified apps from reputable sources, and ensure these devices are regularly updated.
Preparing for an event
Even if you follow every best practice we’ve covered here, it won’t necessarily be enough to prevent a cybersecurity event. New types of cyber attacks are being created constantly and the methods that they employ are increasingly sophisticated and difficult to detect. For this reason, the final step in good digital hygiene is to have a clear plan in place in the event of a cybersecurity breach.
Here are a few steps to follow to ensure you are fully prepared for any event that might occur:
- Identify high-value data — Knowing what data is most likely to be targeted by cybercriminals allows you to ensure increased monitoring and rapid isolation of high-value assets in the event of a breach.
- Create regular back-ups — By backing up data regularly, particularly high-value data, you can ensure that if there is a breach you do not lose access to the only version of that data that you have.
- Have a clear plan in place — Having a set plan to follow if there is a breach allows you to respond quickly and effectively if and when one does occur. Don’t wait until a breach to put an action plan in place, have it ready to go before you need it.
- Run drills — Having a plan is great, but if you have no experience with it, then it may fall flat on the night. Like fire drills, running through your data breach plan before an incident ensures everyone is clear on their roles and responsibilities and will allow for a far more effective response.
- Keep detailed records — Keeping regular, comprehensive records of all of your data and any threats that have been repelled by your cybersecurity software and team will allow you to have a far clearer picture of anything that has been compromised if an event does actually occur.

How JT can help
Having a managed service provider for your cybersecurity takes the guesswork out of digital hygiene. Onboarding an MSP for your cybersecurity services gives you access to a team of experts who constantly monitor your system for signs of attack and stay up to date with the newest developments. This helps you to reduce costs compared to hiring an in-house staff to do the same and offers a more efficient way of protecting your systems.
Choosing JT as your managed service provider for cybersecurity gives your organisation access to a huge range of cybersecurity and networking services, giving you safe, secure, and seamless connectivity.
Book a meeting with our team of experts to discuss your requirements.